Three security levels in new IQRF OS 4.0
16 March 2017
The Internet of Things is still a very young technology area that is not protected well yet. The company MICRORISC, author of the IQRF wireless technology, understands this and works on many ideas how to continually improve the security of its technology and devices built on it.
The next big update of the IQRF operating system, the IQRF OS 4.0 will be released on March 23rd and will be mainly focused on the security. The update will bring for example the AES-128 encryption protocol, which provides security at three different levels – access encryption, networking encryption and user encryption.
Access encryption
Access encryption is used to secure all sensitive OTA network operations. It is used for bonding and only authorized devices and users with valid Access password can join the network or to maintain network devices. CATS services, network backup and restore use Access encryption.
All sensitive data exchanged during bonding, such as network password, NID and Node address are transferred encrypted with access encryption.
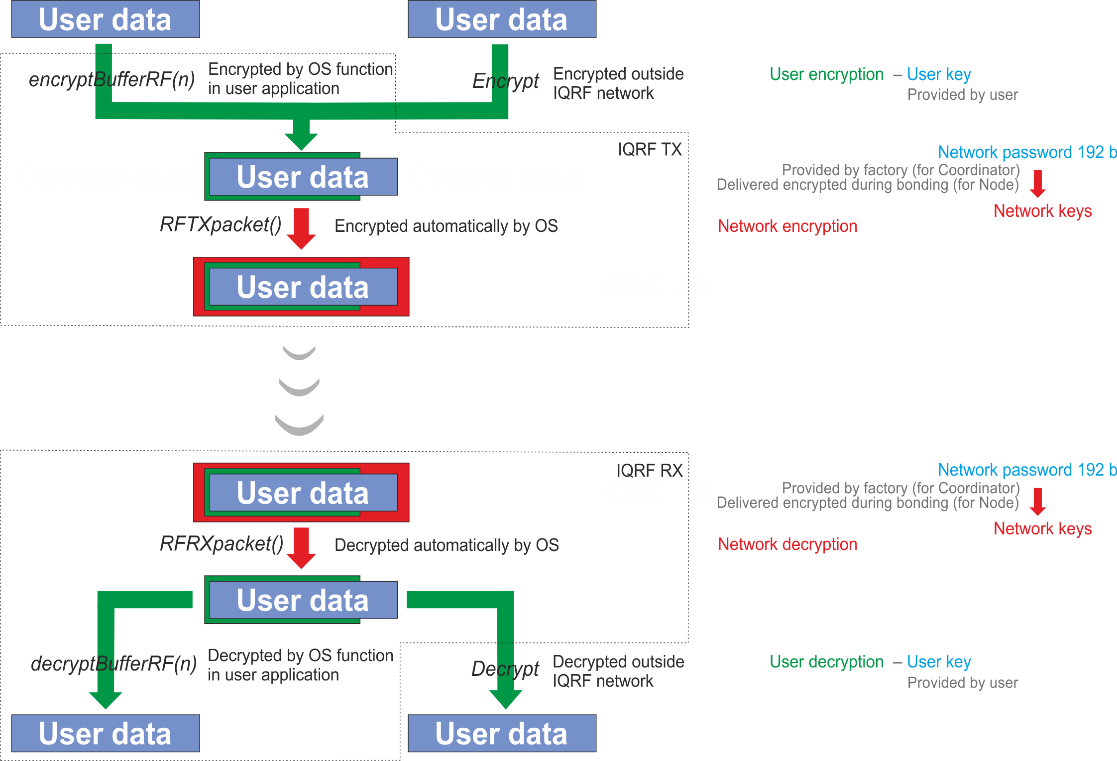
Network encryption
AES-128 with 16 B long keys and additional proprietary CDC (Cipher Data chaining) algorithm is used for Networking encryption. Every TR transceiver is equipped with a 192 b long unique fully random password individually generated at the factory. The 128 b long keys in given network are derived from the password of the Coordinator. The password is passed to Nodes securely, while bonding, encrypted by Access encryption.
User encryption
Besides protection of network communication, there is an optional way to increase privacy by adding another encryption shield to hide user's payload data (either networking or non-networking) or to enhance network protection. User encryption is fully under user's control. It utilizes User key specified by the user. User encryption and/or decryption can optionally be performed outside TR transceivers which allows to hide user's data not only when OTA transferred but also outside IQRF platform.
More news about IQRF OS 4.0 coming soon.
Online webinar - registration is running
CZ language - 30th March, 2017 - 10:00 to 11:30
EN language - 30th March, 2017 - 13:00 to 14:30