IQRF OS 4.0 technical information
21 March 2017
Security
The new operating system IQRF 4.0 brings ultimate security to IQRF networks.
There are three different protections based on AES-128 implemented:
- Access encryption
used for
- bonding
- CATS services
- network backup and restore
- Networking encryption
- User encryption
Compromising of keys is very frequent source of security problems. Therefore, IQRF OS minimizes and protects also manipulation with keys – network and access keys are not known during physical manipulation as they are generated from respective passwords.
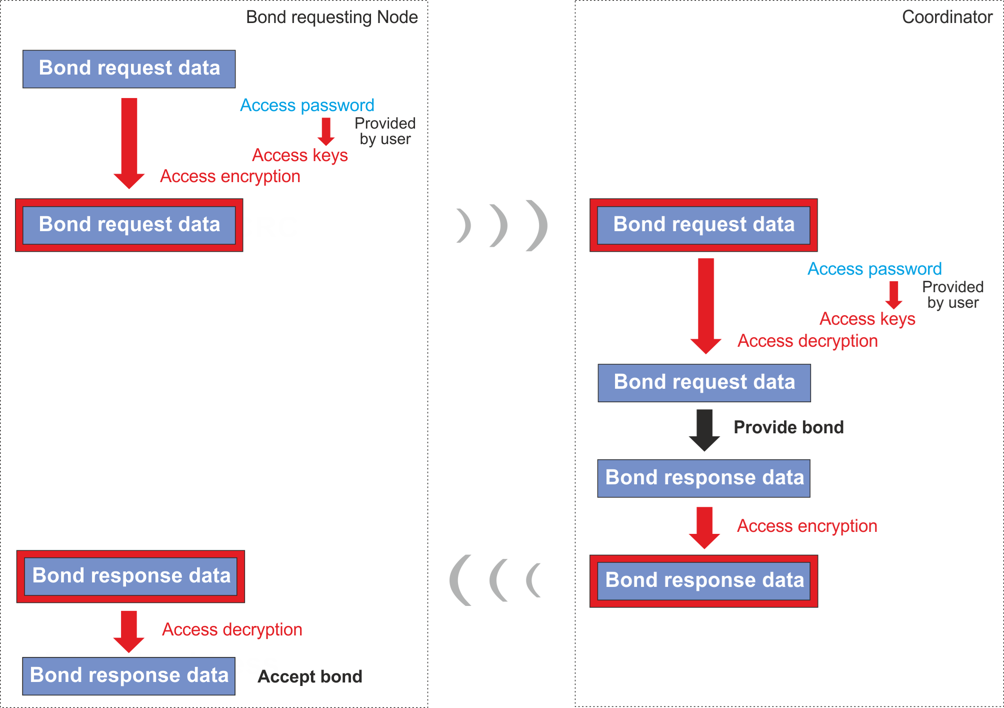
Access encryption
Access encryption is used to secure all sensitive OTA network operations. It is used for bonding and only authorized devices and users with valid Access password can join the network or to maintain network devices. CATS services, network backup and restore use Access encryption.
All sensitive data exchanged during bonding, such as network password, NID and Node address are transferred encrypted with access encryption.
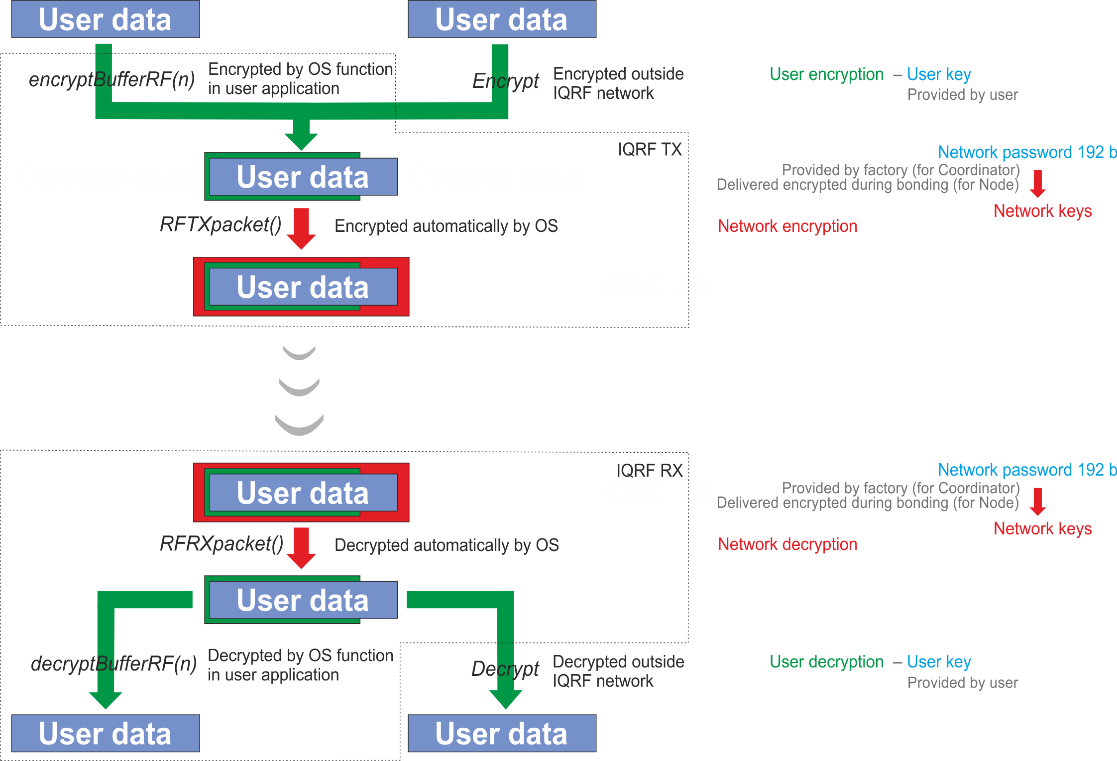
Network encryption
AES-128 with 16 B long keys and additional proprietary CDC (Cipher Data chaining) algorithm is used for Networking encryption. Every TR transceiver is equipped with a 192 b long unique fully random password individually generated at the factory. The 128 b long keys in given network are derived from the password of the Coordinator. The password is passed to Nodes securely, while bonding, encrypted by Access encryption.
User encryption
Besides protection of network communication, there is an optional way to increase privacy by adding another encryption shield to hide user's payload data (either networking or non-networking) or to enhance network protection. User encryption is fully under user's control. It utilizes User key specified by the user. User encryption and/or decryption can optionally be performed outside TR transceivers which allows to hide user's data not only when OTA transferred but also outside IQRF platform.
Other features and changes
- Deep sleep for TR-76D modules
- consumption < 100 nA
- Longer RF range of LP/XLP mode
- the same like for STD mode
- Improved FRC
- 1B FRC downloads data from 63 Nodes
- 2B FRC downloads data from 31 Nodes
- Device cloning canceled
- just upload the appropriate HWP and access password to the transceiver and restore network information from the backup
- DPA demo canceled
- Coordinator/Node as a one device canceled
- IQMESH examples removed from Startup Package
- The only way for IQMESH is DPA.
- Israel (IL) version of TR modules supported
- Basic IQRF header file template-basic.h renamed to IQRF.h
- OS 4.00D is not interoperable with OS 3.08D
- User OS upgrade to version 4.00D is possible, downgrade back to OS 3.08D is not possible
- IQRF IDE 4.40 and DPA 3.30 required
More on: www.iqrf.org