Ecryption in IQRF OS 4.0
17 March 2017
IQRF OS 4.0 brings three different protection layers based on AES-128. It is – access encryption, networking encryption and user encryption. If you want to know more about those protection layers, read it here.
So, what other features in IQRF OS 4.0 are encrypted?
Network passwords are randomly generated with high entropy and delivered encrypted to devices during bonding process.
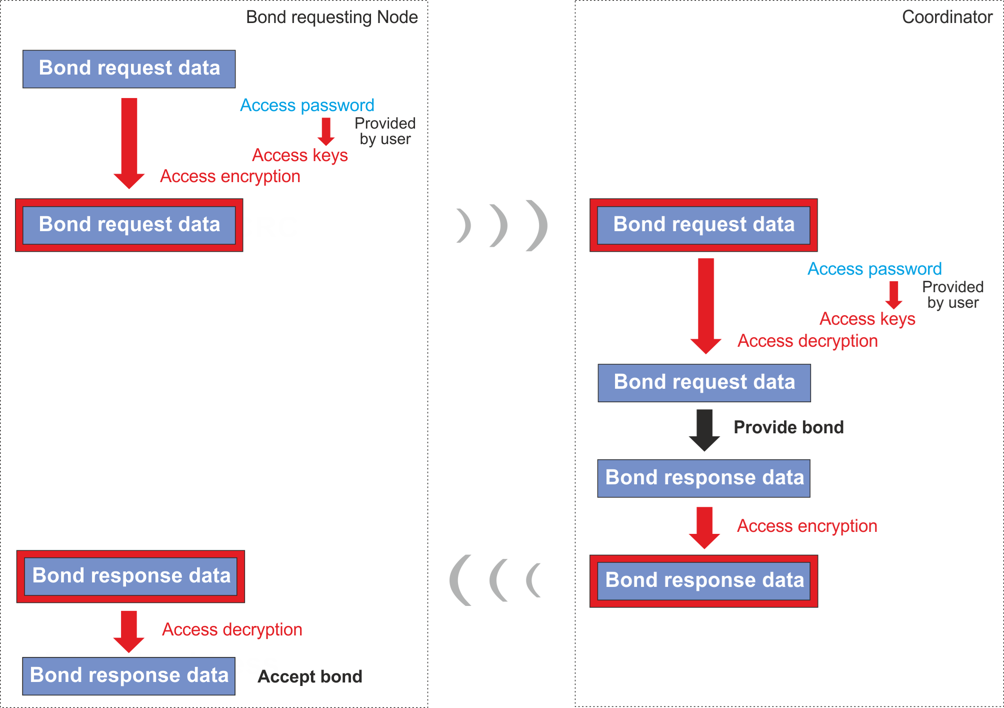
Access encryption is used to secure all sensitive OTA network operations. It is used for bonding, CATS services and network backup and restore.
Networking encryption is the most important part of the whole process of network communication. Network communication is encrypted by OS itself and user don't have to care about it. Thus, every IQRF network is equally highly secured by default. Only systems with valid Network password are allowed to interact with network and individual devices. AES-128 encryption protocol with 16 B long keys is used together with proprietary Cipher Data Chaining algorithm.
User encryption is another option how to improve security of data transmission. This option is fully under user's control. The key, specified by user, is used. This key is unknown for OS to push security level even further. Data transferred inside of encrypted packets are furthermore encrypted by user's key. This makes readability of data impossible both for OS and anyone who doesn't know the user's key. User encryption/decryption can be performed outside TR e.g. in application itself, which ensures safety even beyond the network.